Update IAM settings for your workspace
Please note that this workshop has been archived and is not actively maintained. On September 30, 2026, AWS will discontinue support for AWS App Mesh. For more information, visit this blog post.
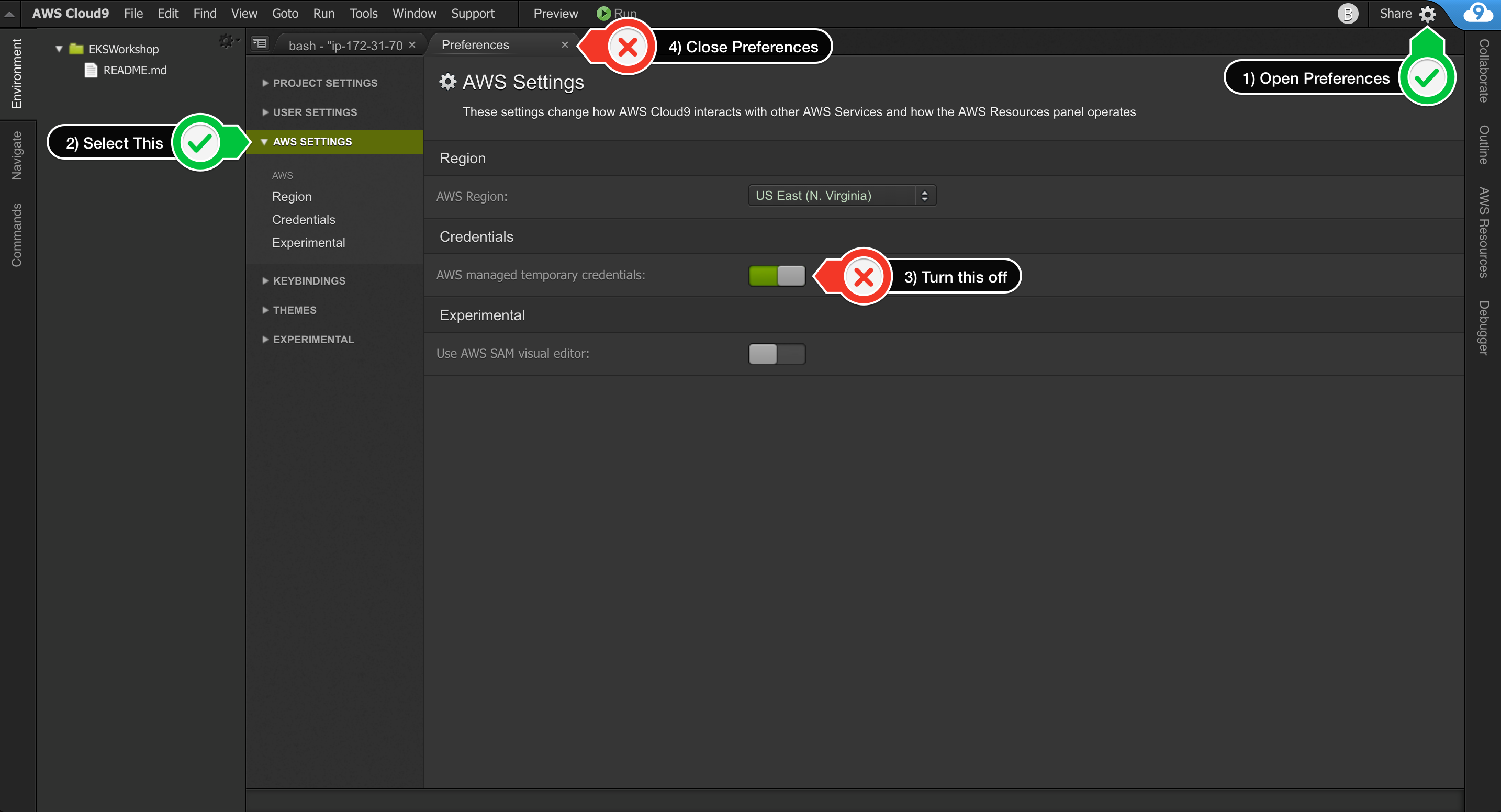
Cloud9 normally manages IAM credentials dynamically. This isn’t currently compatible with the EKS IAM authentication, so we will disable it and rely on the IAM role instead.
- Return to your workspace and click the sprocket, or launch a new tab to open the Preferences tab
- Select AWS SETTINGS
- Turn off AWS managed temporary credentials
- Close the Preferences tab
To ensure temporary credentials aren’t already in place we will also remove any existing credentials file:
rm -vf ${HOME}/.aws/credentials
We should configure our aws cli with our current region as default:
export ACCOUNT_ID=$(aws sts get-caller-identity --output text --query Account)
export AWS_REGION=$(curl -s 169.254.169.254/latest/dynamic/instance-identity/document | \
grep region | cut -d\" -f4)
echo "export ACCOUNT_ID=${ACCOUNT_ID}" >> ~/.bash_profile
echo "export AWS_REGION=${AWS_REGION}" >> ~/.bash_profile
aws configure set default.region ${AWS_REGION}
aws configure get default.region
Validate the IAM role
Use the GetCallerIdentity CLI command to validate that the Cloud9 IDE is using the correct IAM role.
aws sts get-caller-identity
The output assumed-role name should contain:
TeamRole
or
AppMesh-Workshop-Admin
VALID
If the Arn contains the role name from above and an Instance ID, you may proceed.
{
"Account": "123456789012",
"UserId": "AROA1SAMPLEAWSIAMROLE:i-01234567890abcdef",
"Arn": "arn:aws:sts::123456789012:assumed-role/TeamRole/i-01234567890abcdef"
}
{
"Account": "123456789012",
"UserId": "AROA1SAMPLEAWSIAMROLE:i-01234567890abcdef",
"Arn": "arn:aws:sts::123456789012:assumed-role/AppMesh-Workshop-Admin/i-01234567890abcdef"
}
INVALID
If the Arn contains MasterRole, or does not match the role name output above, DO NOT PROCEED. Go back and confirm the steps on this page.
{
"Account": "123456789012",
"UserId": "AROA1SAMPLEAWSIAMROLE:i-01234567890abcdef",
"Arn": "arn:aws:sts::123456789012:assumed-role/AppMesh-Workshop-Admin/MasterRole"
}